· L'équipe de recherche et développement IBM Xforce vient de publier son rapport trimestriel sur son analyse des menaces avancées Ce rapport dévoile qu'au moins 1 milliard de données personnelles identifiables (PII) ont été divulguées en 14 Le rapport 15, qui met également en évidence les résultats du dernier trimestre 14, a recensé plus de 9 0 nouvellesXForce refused to ally with Romany and destroyed the ship, seemingly perishing in the ensuing explosion Soon after, a new team of mediasavvy mutants usurped the name XForce, bringing the original team out of hiding to reclaim their name The new team prevailed and eventually changed their name to XStatix, though by that time the original team had gone their separate waysIBM Security XForce Red hackers Webinar 3 0807T by RUBENS ALVES New Course Roadmaps for Cloud Pak for Security Skills Journey 0 0803T by Wendy Batten Don't miss your latest chance to ask the hackers anything!

Ibm Security Introduces New X Force Red Services For Iot Auto Industry Media Entertainment Services Alliance
Ibm x-force logo
Ibm x-force logo- · Bloomberg the Company & Its Products The Company & its Products Bloomberg Terminal Demo Request Bloomberg Anywhere Remote Login Bloomberg Anywhere Login Bloomberg Customer Support Customer Support · IBM a l'intention de commencer les déploiements de production en mode bêta dès cette année pour tirer partie d'IBM Watson for Cyber Security, avec la collaboration de Sogeti La bibliothèque de recherche de renommée mondiale IBM XForce constitue le noyau dur d'IBM Watson for Cyber Security Cet ensemble de connaissances comprend années de recherche
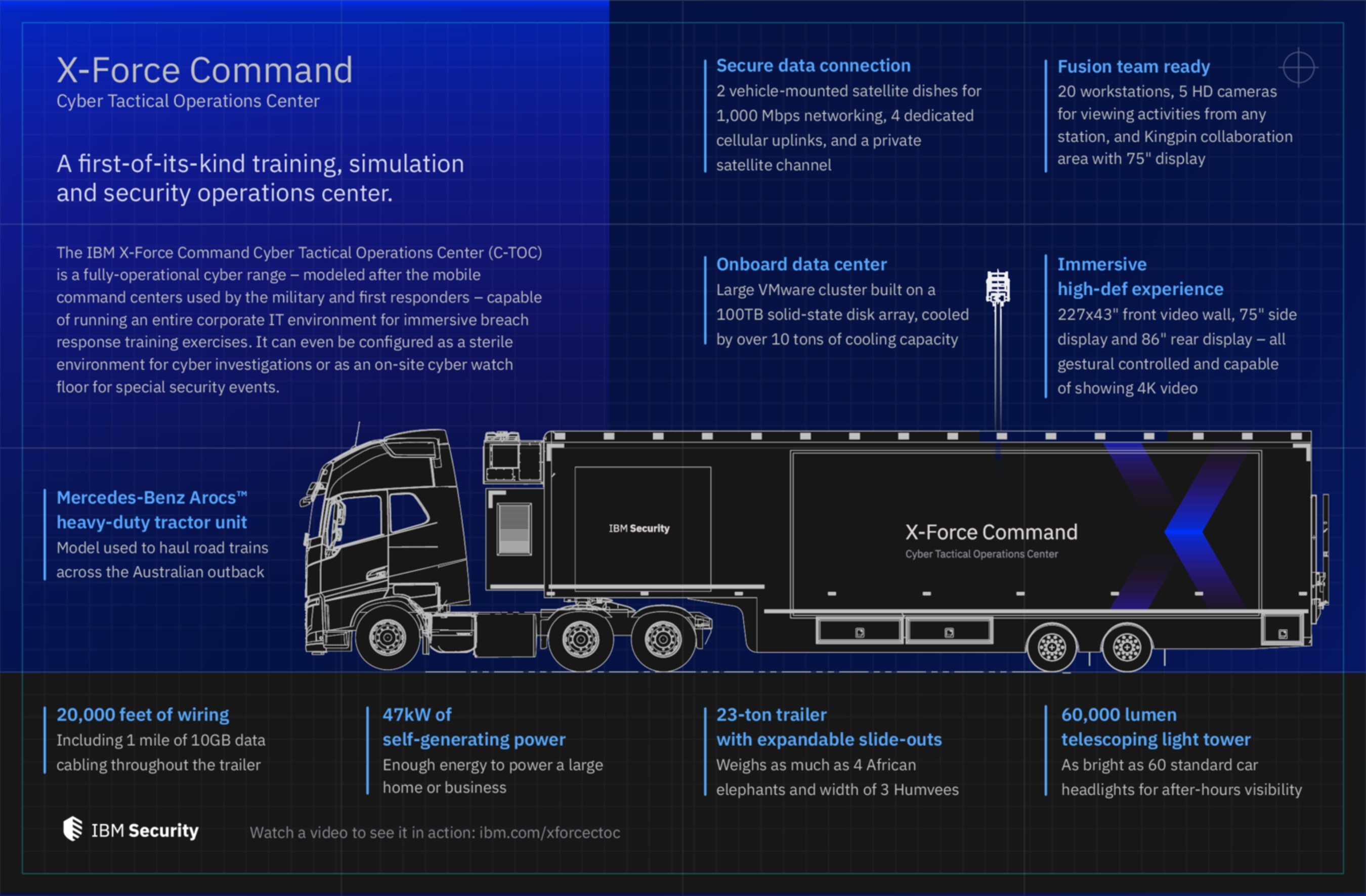



Ibm Has Created A Mobile Tactical Operation For Cybersecurity Emergencies Dzone Security
Health Check Framework (HCF) for IBM Security QRadar SIEM is a tool that allows QRadar users, administrators and security officers to perform periodical and ondemand monitoring of a range of statistical, performance and behavioral parameters of QRadar deployment including AllinOne andSinglesource support services for hybrid IT environments IBM Technology Support Services keeps missioncritical systems running smoothly, including hardware and software from IBM and other OEMs We provide support for hybrid cloud environments that helps simplify your IT support management and adds valueIBM Z & LinuxONE;
DATA SHEET FortiSOAR™ 2 Key Features Visual Playbook Builder FortiSOAR's™ Visual Playbook Designer allows SOC teams to design, develop, debug, control and use playbooks in the mostIBM Security offers one of the most advanced and integrated portfolios of enterprise security products and services The portfolio, supported by worldrenowned IBM XForce® research, enables organizations to effectively manage risk and defend against emerging threats IBM operates one of the world's broadest security research, development and delivery organizations,Learn about the best IBM XForce alternatives for your Threat Intelligence software needs Read user reviews of AlienVault USM, Anomali ThreatStream, and more
· The portfolio, supported by worldrenowned IBM XForce® research, enables organizations to effectively manage risk and defend against emerging threats IBM operates one of the world's broadest security research, development and delivery organizations, monitors 35 billion security events per day in more than 130 countries, and holds more than 3,000 security patents · © Copyright IBM Corporation 15 IBM Security Route 100 Somers, NY 105 Produced in the United States of America June 15 IBM, the IBM logo, ibmcom, AppScan, QRadar, Trusteer, and XForce are trademarks of International Business Machines Corp, registered in many jurisdictions worldwide Other product and service names might be trademarks of IBM or other companies A current list of IBM trademarks is available on the web at "Copyright and trademark information" at ibm · You may recall that back in February a panel of IBM Security XForce Red hackers presented an "Ask Our Hackers Anything" webinar Nearly 300 security professionals attended, and the demand for a followup session was immediate If you missed that session or have spent the months since brainstorming more great questions for the hackers, then we have some good




Ibm X Force Threat Intelligence Ibm




X Force Red In Action Spotlight On Penetration Testing With Space Rogue Security Intelligence
IBM XForce Cyber Tactical Operations Center Wins a 19 Edison Award Recognized all over the world for excellence in innovation, IBM's groundbreaking mobile cyber training center continues to turn heads In 18, Diversified was awarded the opportunity to work with longtime partner IBM once again on their newest initiative—the XForce Cyber Tactical Operations Center (CTOC) · SAN FRANCISCO – IBM THINK 19, Booth #516 – Feb 12, 19 – Qualys, Inc (NASDAQ QLYS), a pioneer and leading provider of cloudbased security and compliance solutions, today announced that XForce Red, IBM Security's team of veteran hackers, will integrate Qualys' new groundbreaking Patch Management solution with XForce Red's Vulnerability ManagementProvide contextual information curated by IBM XForce IRIS team • Prioritize threats with XForce Threat Score, an adaptive score, calculated based on your relevance, severity, penetration, impact and actual environmental sightings • Identify threats active in your environment with Am I Affected, which runs continuous and automated searches across connected data sources • Work from a




Ibm Security Announcing Ibmxforce Red Ibm S New Security Testing Team Learn More Here T Co Gvmumluu3s




Ibm X Force Threat Intelligence Index Archives Electronic Health Reporter
· IBM XForce Threat Intelligence Why Insider Threats Challenge Critical Business ProcessesRetrouvez toutes les actus IBM news, livres blancs, dossiers, analyses Toute l'actualité IT sur Siliconfr186 offre d'emploi IBM Montréal, QC disponible sur Indeedcom Project Coordinator, System Programmer, Mainframe Systems Engineer




Ibm Security X Force Threat Intelligence Reviews Ratings Alternatives Gartner 21
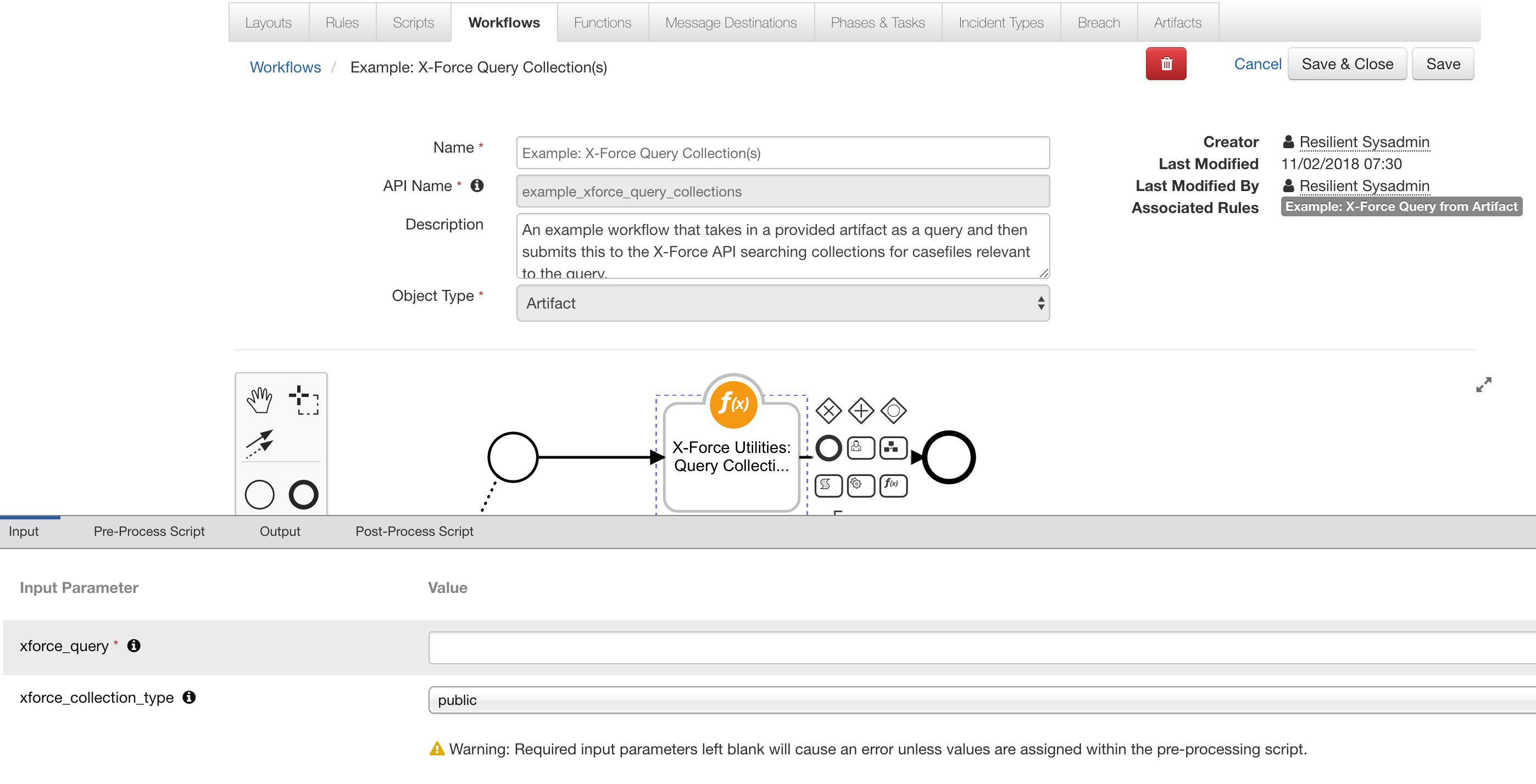



Ibm Security App Exchange X Force Collections For Soar
1 0803T0500 by Jennifer TullmanBotzer RESTRICTED userid 1 0803T0100 by Scott Tietjen Original · La plateforme de gestion de la fraude d'IBM est une offre unique qui réunit les fonctionnalités Big Data et Analytics d'IBM pour aider les organisations à regrouper des données à partir de sources externes et internes et à appliquer des analyses sophistiquées pour prévenir, identifier et analyser les activités suspectes Capable de détecter des relations non évidentesThe IBM XForce team analyzes trends in attack behaviors across platforms and industries, providing insights on the most significant security threats




Allesao Integrations Phoenix Cybersecurity Managed Sao



Ibm X Force Github
· IBM XForce Incident Response & Intelligence Services (IRIS) a aidé les clients à exécuter les répétitions IR et les a adaptées à l'environnement unique de chaque client Cela comprend des répétitions complètes et exécutées à distance des plans IR conçus pour résister à la tempête actuelle De plus, IBM XForce IRIS aide les clients avec une assistance téléphonique · IBM XForce Exchange Infographic 1 Realtime global intelligence from over 270 million endpoints IBM XForce Exchange 65%use external threat intelligence source as part of their security analytics activities3 51%believe it's imperative to share threat intelligence with industry peers4 of CISOs of enterprises 9,0 In 14, a record number of new vulnerabilities were recorded5 IBM · IBM a pris ce parti avec son « centre d'opérations cybertactiques » XForce Command ouvert depuis 16 aux ÉtatsUnis, à Boston Décliné en une version nomade, il
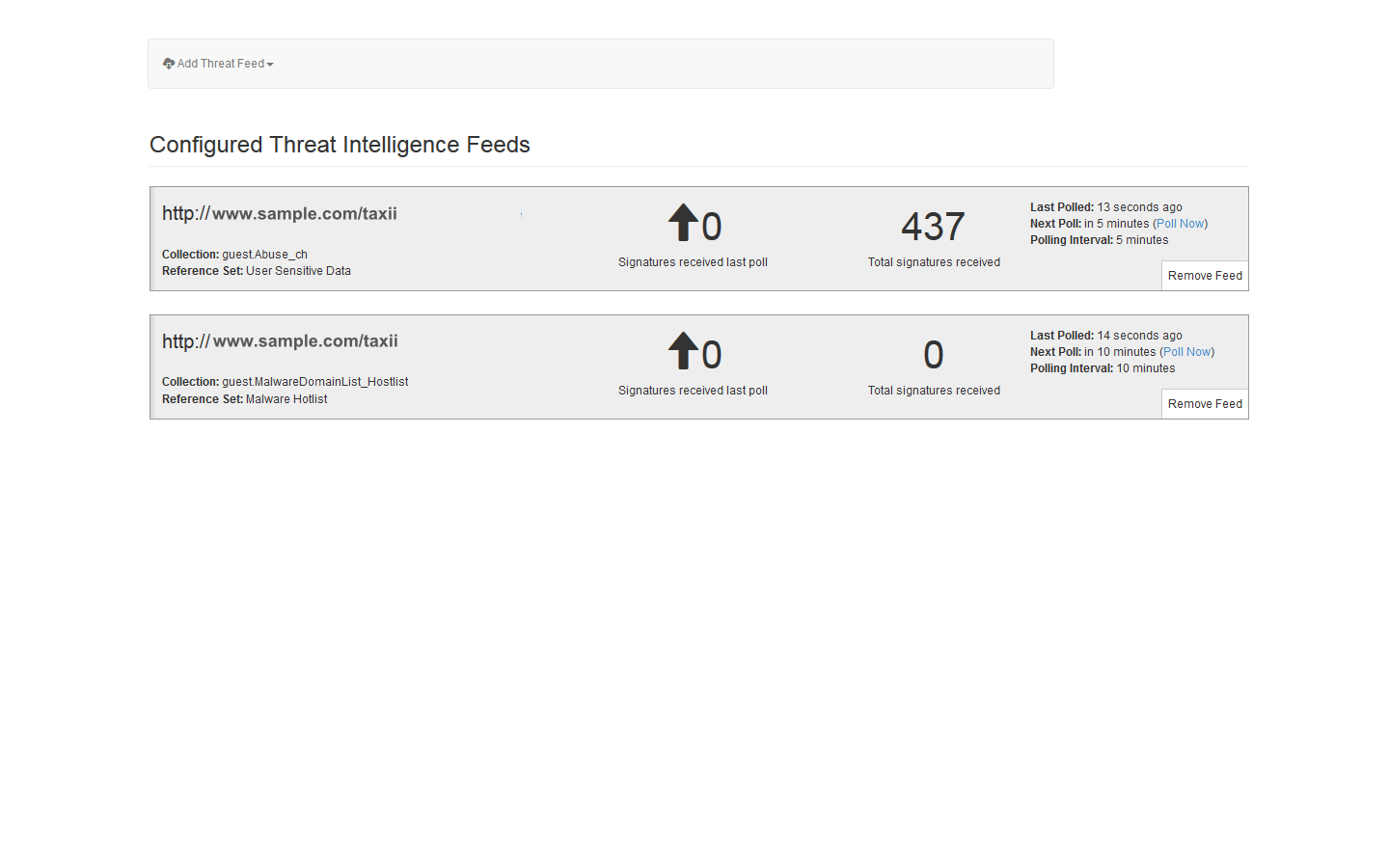



Ibm Security App Exchange Threat Intelligence




Ibm X Force Threat Intelligence Ibm
3 ©Copyright IBM Corporation 14 All rights reserved IBM and the IBM logo are trademarks or registered trademarks of the IBM Corporation in the United States, · CAMBRIDGE, Mass, April 27, 17 /PRNewswire/ IBM (NYSE IBM) Security today announced research from its IBM XForce Research team which revealed the financial services industry was attacked more than any other industry in 16 65 percent more than the average organization across all industries · IBM Security has released the IBM XForce Threat Intelligence Index , highlighting how cybercriminals' techniques have evolved after decades of access to tens of billions of corporate and personal records and hundreds of thousands of software flaws According to the report, 60% of initial entries into victims' networks that were observed leveraged either




Gain Actionable Threat Intelligence Utilizing Dflabs Soar And Ibm X Force Exchange Dflabs




X Force Red Offensive Security Services Ibm
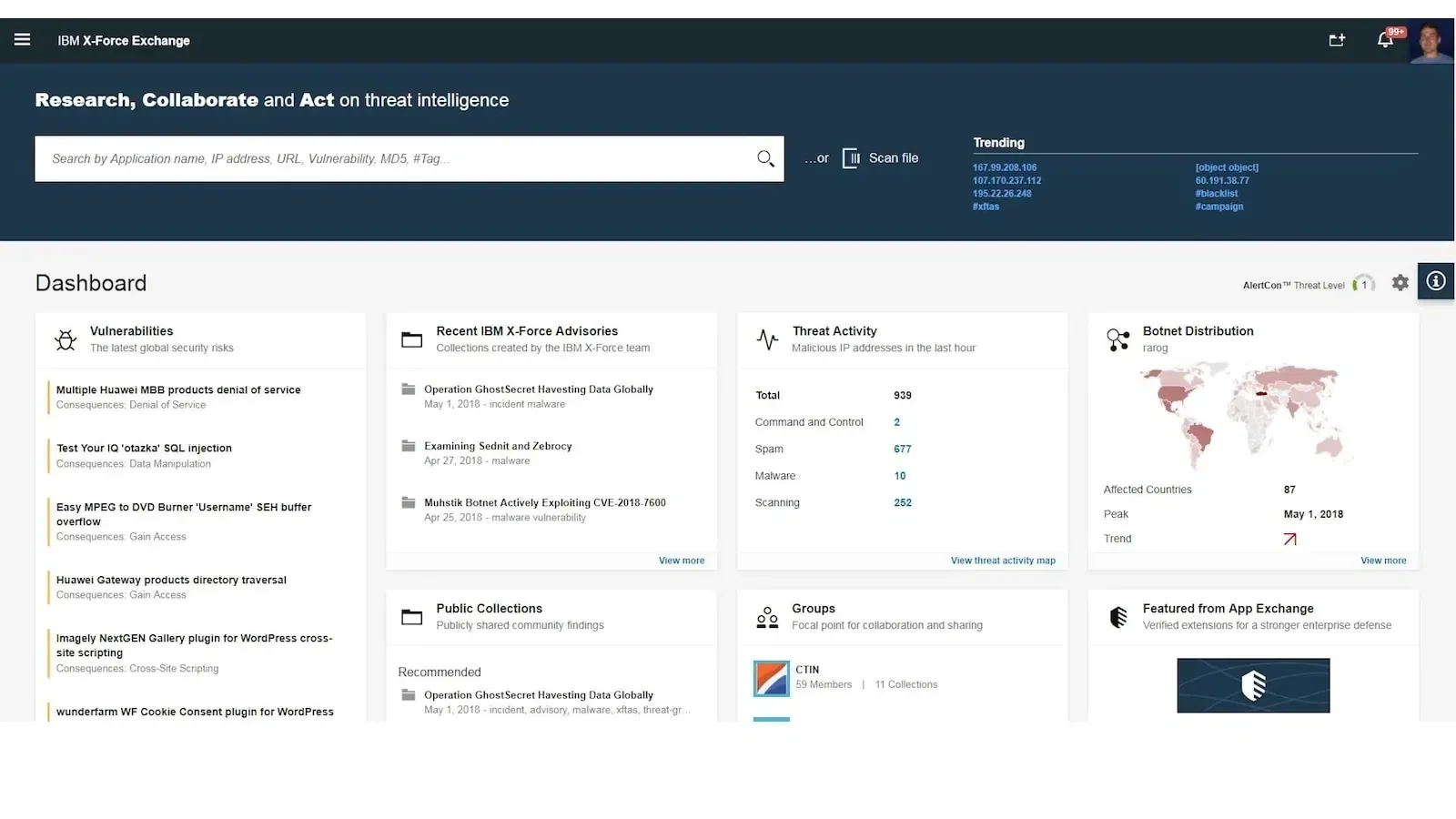
/03/19 · IBM XForce Exchange is a cloudbased threat intelligence sharing platform enabling users to rapidly research the latest security threats, aggregate actionable intelligence and collaborate with peers IBM XForce Exchange is supported by human and machinegenerated intelligence leveraging the scale of IBM XForce IBM XForce is also known as XForceIBM XForce หรือหน่วย Threat Intelligence ของ IBM ได้จัดทำรายงานในปี 18 เพื่อชี้วัดดัชนีการโจมตีในรอบปีที่ผ่านมาพบว่าคนร้ายนิยม RansomwareTalos® and IBM XForce® Exchange to further strengthen detection for all of the products This comprehensive and integrated toolset enables security teams to achieve faster, more intelligent incident response and mitigation Professional services and managed services These technical capabilities are supported by Cisco and IBM's services organizations and business partners




Ibm X Force Cyber Security Training On Wheels Ibm Nordic Blog




Infographic Ibm X Force Exchange
The XForce Exchange (XFE) API provides programmatic access to XForce Exchange Each call in the API supports a capability in the UI of the XForce Exchange platform The API follows guidelines for RESTful APIs, with the HTTP path defining the service to · Bloomberg the Company & Its Products The Company & its Products Bloomberg Terminal Demo Request Bloomberg Anywhere Remote Login Bloomberg Anywhere Login Bloomberg Customer Support Customer Support · Event Streams applies the provided security and vulnerability patch updates to the client cluster, according to IBM XForce timeframes Manage users and access Customer is responsible for managing your organizational account users and related access to the Event Streams instance Compliance controls Customer is responsible for maintaining your organizational compliance controls IBM




Ibm X Force Stolen Credentials And Vulnerabilities Weaponized Against Businesses In 19




Partners
Cloud Pak for Data; · IBM Corporation logo (PRNewsFoto/IBM Corporation) (PRNewsFoto/) The new team will be led by IBM's Charles Henderson, a worldrenowned penetration testing expert IBM XForce Red is a global team · IBM XForce monitors billions of spam emails a year, mapping trending, malicious campaigns and their origins Recent analysis from our spam traps uncovered a new Trickbot campaign that currently




Ibm Security Solutions




Dnif Threat Intelligence Firecompass
IBM, the IBM logo, ibmcom, and XForce are trademarks of International Business Machines Corp, registered in many jurisdictions worldwide Other product and service names might be trademarks of IBM or other companies A current list of IBM trademarks is available on the web at "Copyright and trademark information" at ibmcom · State of the Phish IBM XForce Reveals Current Phishing Attack Trends Phishing has long been an infection vector of choice for threat actors, and for good reason — itIBM XForce Exchange est une plateforme de partage de renseignements sur les menaces basée sur le cloud qui permet aux utilisateurs de faire des recherches rapides sur les menaces les plus récentes en matière de sécurité, de rassembler des renseignements utiles et de collaborer avec leurs homologues IBM XForce Exchange se base sur des renseignements d'origine humaine et générés par une machine exploitant l'évolutivité d'IBM




Key Findings From The Ibm X Force Threat Intelligence Index 18




Ibm X Force Threat Intelligence Ibm
IBM XForce Exchange is a threat intelligence sharing platform enabling research on security threats, aggregation of intelligence, and collaboration with peersThreat research teams, Cisco Talos® and IBM XForce Even with these controls, there is always the risk of ransomware getting in, but Cisco and IBM have extensive tools to help organizations respond with speed and confidence Better together IBM Security and Cisco have partnered to address the growing need for deeper collaboration Chief Information Security Officers (CISOs) areSecuring an organization can often feel like a precarious climb IBM Security's incident response and threat intelligence services apply proactive threat intelligence, incident response, threat hunting, and consultation services to help your organization prepare for, detect, and respond to whatever cyber incidents come your way




The Ibm X Force 16 Cyber Security Intelligence Index




Ibm Opens New Cambridge Ma Security Headquarters With Massive Cyber Range Techcrunch
The IBM XForce Mission § Monitor and evaluate the rapidly changing threat landscape § Research new attack techniques and develop protection for tomorrow's security challenges § Educate our customers and the general public § Integrate and distribute Threat Protection and Intelligence to make IBM solutions smarter · Ransomwares, menaces internes Avec 31% des cyberattaques observées par IBM Security XForce, l'Europe a été la région du monde la plus ciblée en IBM Security a publié la plus récente édition de son rapport sur l'évolution des menaces mondiales de cybersécurité Rapport XForce Threat Intelligence Index 21 L'année a sans aucun doute été l'une desAbout Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy & Safety How works Test new features Press Copyright Contact us Creators




Ibm X Force Exchange Integration Trustar




Ibm Unveils New Solution To Secure Blockchain And Connected Infrastructure
IBM XForce Red is seeing that 70 percent of solutions that incorporate blockchain rely on traditional technologies for backend processes like authentication, data processing and Application Programming Interfaces (API) The XForce Red Blockchain Testing service will evaluate the whole implementation including chain code, public key infrastructure and hyperledgers XForce Red




Ibm X Force Insights From The 1q 15 X Force Threat Intelligence Qu



Github Ibm Xforce Xfe Node Node Js Sdk For Ibm X Force Exchange




Ibm Mobile Soc Delivers Cybersecurity Incident Response Training Mssp Alert




Ibm X Force Red Automotive Testing Ibm




Ibm X Force Threat Intelligence Ibm




Ibm X Force Raises Internet Security Alert Con 10 12 12 10 12 By Caleb Barlow Technology




Ibm Has Created A Mobile Tactical Operation For Cybersecurity Emergencies Dzone Security




Ibm Security S X Force Threat Index Apac Insights Youtube



Ibm X Force Threat Intelligence India Ibm




Ibm X Force Exchange Ibm X Force Logo Hd Png Download Free Download On Pngix




Ibm Security Logo American Security Today




Command Center Mobile Cyber Range Ibm




Qradar X Force Frequently Asked Questions Faq




Ibm Security Introduces New X Force Red Services For Iot Auto Industry Media Entertainment Services Alliance




Ibm Releases The Annual Ibm X Force Threat Intelligence Index Cyber Risk Leaders



Ibm X Force Exchange




Ibm X Force Exchange Integration Lastline




X Force Threat Intelligence Index Reveals Top Cybersecurity Risks Of




Ibm X Force Exchange Overview Ibm




Ibm S X Force Red Is Coming To Four New Locations




Ibm X Force Exchange Overview Ibm




Ibm X Force Exchange Overview Ibm




Ibm X Force Exchange Overview Ibm



Ibm X Force Threat Intelligence India Ibm




Ibm Security Opens Network Of Four Secure Testing Facilities Globally




X Force Red In Action Spotlight On Penetration Testing With Space Rogue Security Intelligence




Ibm Security Ibm X Force Exchange Sc Media




Ransomware Attacks Decline As Cryptojacking Grows Ibm X Force Reports




Ibm X Force Red Security Team Takes On Security Challenges With The Help Of Ibm Cloud X Force Ibm Computer Network




Ibm X Force Exchange Overview Ibm




Ibm X Force Fortisoar 1 0 1 Fortinet Documentation Library




Ibm X Force Logo




A Portal To A Portal Ibm X Force Exchange




Bostinno An Inside Look At Ibm Security S New Global Hq In Cambridge




X Force Threat Intelligence Index 21 Securityhq Ibm Gold Business Partner



Ibm X Force Threat Intelligence Index Bankinfosecurity




Ibm X Force Red Launches New Service For Blockchain Security Testing Cdsa Media Entertainment Services Alliance



Threat Intelligence Archivi Page 8 Of 8 Dflabs




Ibm Security App Exchange




Ibm Announces New Security Testing Group X Force Red
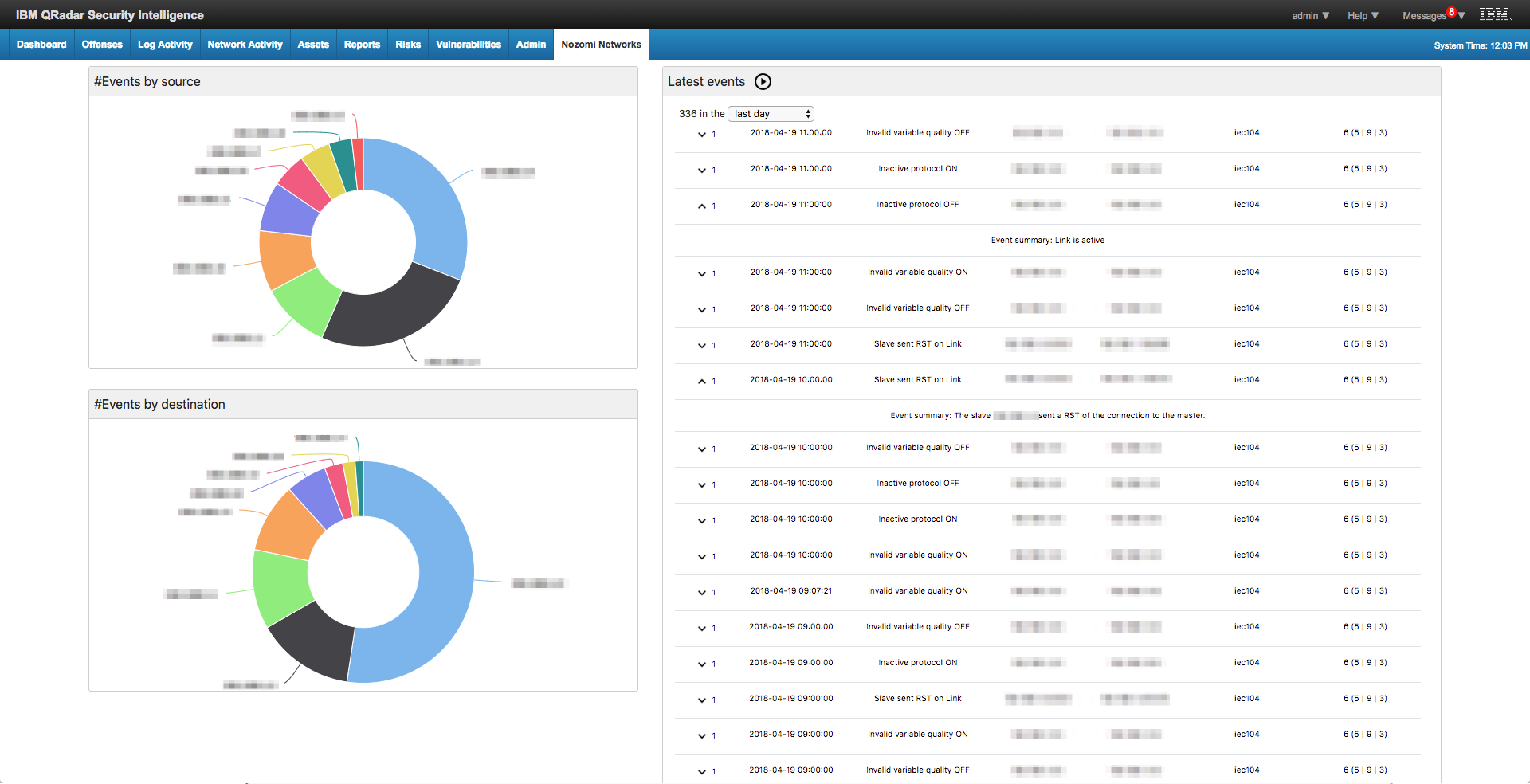



Ibm X Force Logo




Ibm X Force Exchange



Ibm X Force Red Portal




Cyber Simulation Icrmc Bermuda




X Force Exchange Threat Intelligence Speed Security Investigations Youtube




Ibm X Force Threat Intelligence Index 17




Qradar X Force Frequently Asked Questions Faq




Ibm Security Command Centers Ibm
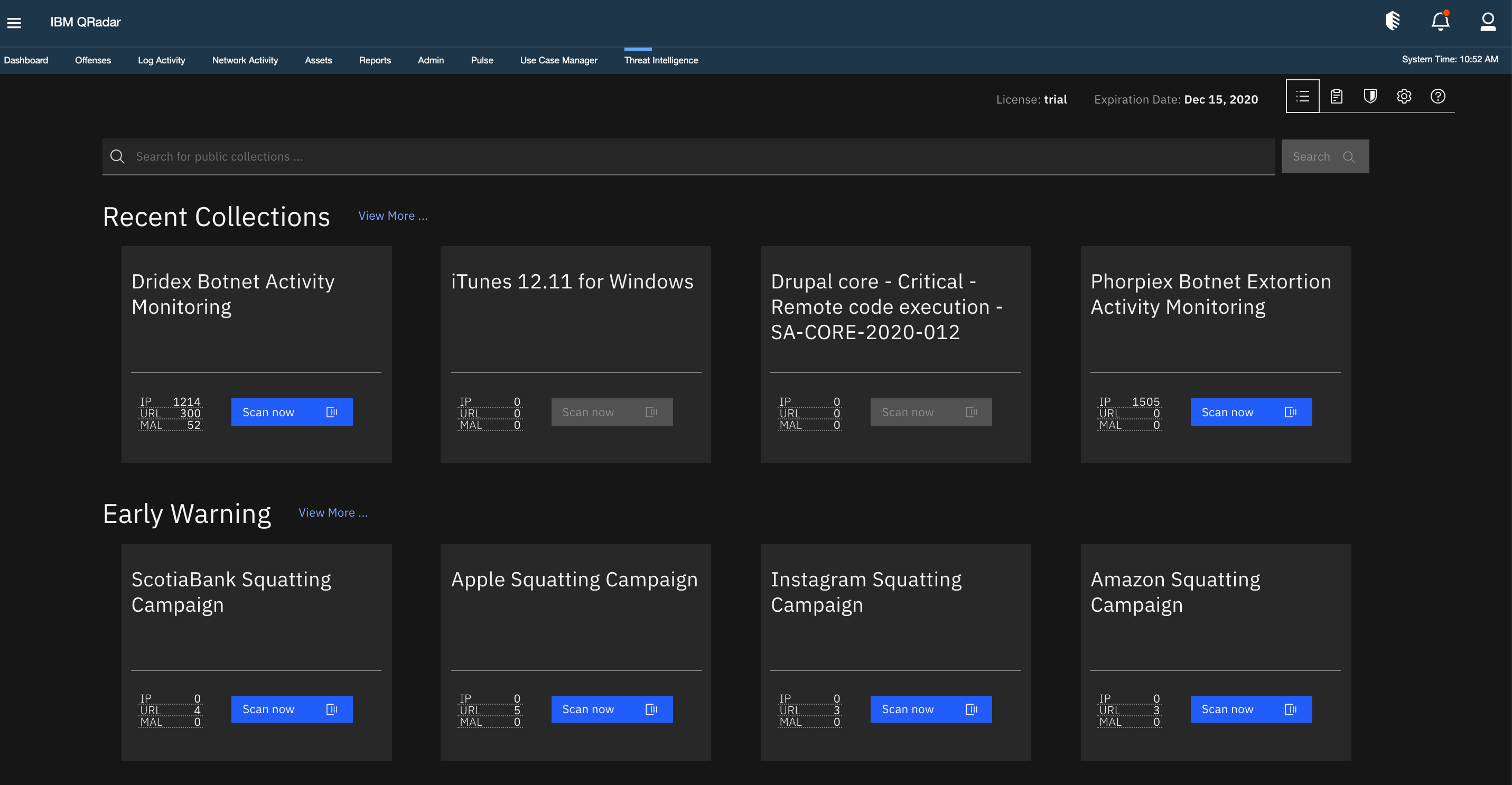



Ibm Security App Exchange Threat Intelligence




Ibm X Force Threat Management A Smarter Security Solution To Manage The 360 Degree Threat Lifecycle




Ibm X Force Logo



Ibm Released The X Force Threat Intelligence Index For The Year




18 Ibm X Force Report Shellshock Fades Gozi Rises And Insider Threats Soar




Ibm X Force Threat Management A Smarter Security Solution To Manage The 360 Degree Threat Lifecycle




Ibm Badges




Ibm Builds Soc On Wheels To Drive Cybersecurity




Ibm X Force Red Unveils Blockchain Security Testing Tool Cryptocurrency




Ibm Launches X Force Threat Management Services For Iot Ot Mssp Alert



Ibm Security Boca Raton Florida United States Of America Businesslive Showcase On Inxero




X Force Threat Intelligence Fight Insider Threats Protect Your Sen




Ibm X Force Intelligence Bisinfotech




Ibm Xforce Q4 14




Ibm Builds Soc On Wheels To Drive Cybersecurity




Ibm X Force




Inside Job Insights On Insider Threats From The Ibm X Force




Ibm X Force Exchange Commercial Api Subscription License 1 Month Tech D1niill Security Cdw Com



Ibm Releases X Force 12 Mid Year Trend And Risk Report Reveals Sharp Increase In Browser Related Exploits Siliconangle




Ibm Releases X Force Threat Intelligence Index To Outline Cyber Vulnerabilities Wendi Whitmore Quoted




Ibm Report Shows Need For Disaster Recovery Strategy




Ibm X Force Logo




Ibm Security Announcing The Ibm X Force Exchange Open Beta Crowd Sourced Information Sharing At It S Best Ibminterconnect Http T Co Js0oxvupvz




Stolen Credentials And Vulnerabilities Weaponized Against Businesses In 19 Ibm Aptantech



Ibm X Force Exchange Reviews And Pricing 21



0 件のコメント:
コメントを投稿